Table of Contents
Point-of-sale software has become a must-have item for every retail business, restaurant, and safe. Up-to-date sales solutions go further than just processing payments; they now structure and automate the whole cycle of your supply chain.
With custom POS development, your opportunities to create self-sufficient and powerful solutions are limitless.
At the same time, despite the development’s capacities, you should still pay attention to the basics, namely POS security and compliance.
At its core, any POS solution is designed to work with considerable volumes of sensitive data, whether it belongs to the company or its clients.
Overlooking security measures and corresponding compliance may lead to severe financial and reputational losses for the organization.

Altamira has completed several POS development projects. In this article, we’ve collected the main insights on point-of-sale security and described the measures we take to ensure POS security and data protection.
Why should you pay attention to data security in POS systems development?
POS security is a valid point to consider at every stage of POS development. As a payment processing and data storage software, it gains access to personal identifiable information (PII), such as clients’ and employees’ full names, credit card numbers, phone numbers, ID numbers, emails, social security numbers, etc.
Insufficient security measures may jeopardize the safety of such types of data. POS systems are known and easy targets for hackers, as this software is quite popular among various types of merchants and always has value hackers may take advantage of.
Traditional POS systems are vulnerable and succumb to malware attacks when malware such as Dexter, vSkimmer, Backoff, PoSeidon, or UDPoS infiltrate devices, track and copy sensitive data (mainly cardholder data), and transfer it to scammers’ command centres.
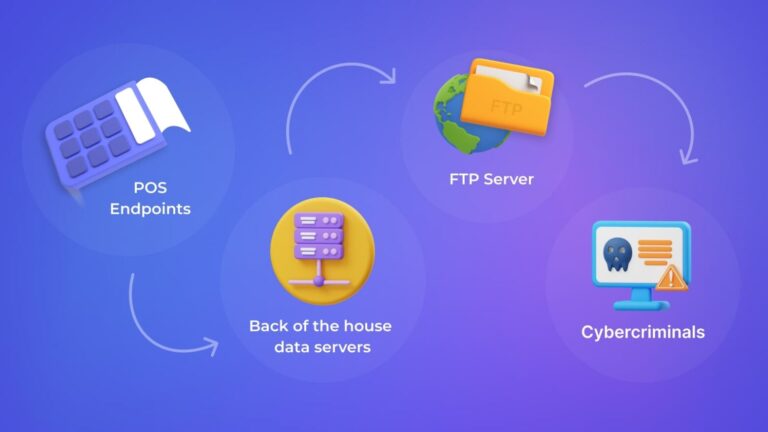
POS vendors often underplay POS security, which leads to data breach cases that regularly appear on the news. Unfortunately, cybersecurity is typically overshadowed by other development concerns, as companies tend to only consider it when they encounter the hacks themselves.
Such an attitude is counterproductive and bound to major detrimental problems. One of the latest exemplary cases has happened with Dickey’s, the US barbecue restaurant chain.
Through a POS-targeted attack, the intruders accessed the credit card information of 3 million of the restaurant chains’ customers and later posted the information online for public access.
As a result, the company was obligated to pay $2.35 million to settle a class-action lawsuit that was filed against them in the aftermath.
So, unreliable POS data protection can undermine all efforts in POS development. Even the most innovative and demanded system won’t survive overturning customers’ PII and will lose any credibility in the eyes of current and potential customers.
Hence, if you plan on starting POS development or already are in the middle of such a project, be sure to pay attention to security and compliance considerations and choose vendors who include POS security requirements in their scope of work.
PCI DSS compliance for POS system security
The industry itself created and implemented standards that should enhance the security of consumers’ credit card data. PCI DSS is the main standard for any business that accepts credit card payments.
What is PCI DSS Compliance?
PCI DSS stands for Payment Card Industry Data Security Standard. It first appeared when major card payment processing companies joined their efforts to create a unified standard to encourage merchants to guarantee a sufficient baseline level of data protection.
It’s important to note that PCI isn’t a law but a security standard. However, it is mandatory for businesses around the world.
Non-compliance may lead to severe fines by card issuers or increased bank transaction fees. And in case of data breaches, you may be charged with additional regulatory fines.

There are four levels of PCI compliance, each of them having different procedures for reporting compliance.
The levels depend on the volume of payment card processing within a year. For example, the first level includes enterprises with more than 6 million transactions per year and requires an external audit by a licensed assessor.
Conversely, businesses on levels 2-4 with less than 6 million transactions annually are obligated to complete self-assessment questionnaires.
What are the PCI Requirements for POS security?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of regulations that all merchants handling card transactions must adhere to in order to ensure secure processing, transmission, and storage of cardholder data.
However, compliance with PCI DSS alone is not sufficient when it comes to the development of software for point-of-sale systems, which are integral to handling payments.
To address the specific needs of secure software development, the Payment Card Industry Security Standards Council introduced the PCI Secure Software Standard, which is now part of the broader PCI Software Security Framework (SSF).
This framework focuses on ensuring that any software handling card transactions are built with security in mind from the ground up, especially for POS systems that process card information.
The PCI Secure Software Standard applies to all software involved in payment processing, including POS terminals, which are often the first point of contact for card data.
Key areas that must be addressed to meet the PCI Secure Software Standard include the identification of critical assets, such as sensitive card data and transaction records, and ensuring that the software is configured securely by default, reducing the risk of vulnerabilities that can be exploited.
Another fundamental requirement is the protection of sensitive data, which includes encrypting cardholder information both in transit and at rest, ensuring that it cannot be accessed by unauthorized parties.

Additionally, multi-factor authentication (MFA) and access controls are mandated to prevent unauthorized access to the software or the systems where card data is processed.
Attack detection mechanisms must also be in place to identify and respond to potential threats in real time.
Finally, vendors are required to provide security guidance to ensure that merchants and software users are aware of how to maintain security throughout the software’s lifecycle.
To cut a long story short, the core requirements dictate how the software development vendor should handle the following aspects:
- critical asset identification;
- secure default configuration;
- sensitive data protection;
- multi factor authentication and access control;
- attack detection;
- vendor security guidance.
By adhering to these requirements, vendors can ensure the security of their POS systems, reducing the risk of breaches and fraud while maintaining compliance with PCI standards.

GDPR as a Regulation for POS Data Protection
GDPR, or General Data Protection Regulations, was introduced in the EU in 2018. It’s another regulation to protect personal information, but it is more far-reaching than the standards set by PCI DSS.
The GDPR definition of personal data includes name, date of birth, phone number, address, ID and insurance numbers, bank details, and recording of the person, among other things.
Moreover, it additionally highlights “special category data” that includes race, religious and political beliefs, sexual orientation, biometric, genetic and health data, etc.
The organization should legitimately prove the need to gain access to this data.
This regulation is applicable to any organization that has an office in the EU or processes the data of EU citizens.
Hence, even if you plan to release your POS system on a non-European market, there is always a chance that the users of your software will encounter customers with EU citizenship.
To prevent possible harmful outcomes from improper data storage, we also suggest following GDPR compliance.
The security framework is firmly integrated into Altamira’s development process customs. Our team of business analysts always includes security and data protection measures in the scope of any project.
Check this article to learn more about our secure software development practices.
Non-functional requirements on POS security and compliance Altamira uses
As you can see, taking adequate measures is an integral part of ensuring POS security.
However, during project inception, you and your vendor might choose to focus on the functionality of your software, its architecture, and solution design.
To ensure that your chosen vendor won’t neglect or miss security and compliance, we suggest that you pay close attention to non-functional requirements (NFRs) in the project documentation.
This type of requirement reflects the system’s attributes like usability, security, compliance, performance, maintainability, legibility, capacity, availability. They don’t reflect functional requirements like Stories, Epics, etc.
However, NFRs still play a significant role in the development as they determine the operations of the whole system.
So, when you receive a proposal, research in addition to the discovery stage or any other documents, check NFRs, especially the ones marked under “security” and “compliance”.
Here are a few examples of what we include into NFRs crucial for POS security solution development:
- System designed to comply with all regulatory and legal requirements, including PCI DSS, GDPR, etc.;
- WAF and DDOS protection by using AWS WAF Firewall V2 Tier and DDoS Protection Basic;
- CSRF protection by single-use token provided on-site login and required for all subsequent API calls;
- Static code analysis through IDEs and build reports using SonarQube;
- Inactivity timeouts with inactive sessions no longer than 168 hours, upon completion autologin performed;
- Web vulnerability scans as part of the development cycle;
- Strict application password policy;
- Two-factor authentication.
In any case, we pick the NFRs specifically for every project, as a disbalance in non-functional requirements can cause problems.
Over-specified NFRs may be unreachable or increase the cost of the development significantly. In turn, under-specified ones may lead to non-working, vulnerable software.
Hence, our business analysts analyze every project separately and form specific NFRs that will contribute with solution use cases, goals, development plans and timelines, internal policies of the client, POS security, etc.
Altamira as an experienced POS development vendor
Altamira is a reliable IT vendor with more than 10 years of experience. We specialize in custom software development for businesses that want to automate their processes and grow their revenues.
We have successfully completed several POS security solution development projects. Let us introduce one of them.
The client has reached out to us with a SaaS POS solution that at the moment was available to be accessed only in the web version. With the growing spread of mobile devices, the company has come to understand that a mobile version of their POS is a must to stay competitive and provide their end-point users with the expected level of services.
Our team has created an IOS version of the software that was connected to the back end of the original SaaS solution. Combined with efficient UI/UX design, the application became a functional and user-friendly logical extension of ZempCenter’s SaaS product.
Our POS development services
We are ready to contribute our generated expertise to your POS development project. We offer:
- custom POS development;
- mobile POS development;
- SaaS POS development;
- development of POS solutions for cloud and dark kitchens;
- upgrading and redevelopment of legacy POS solutions;
- POS integration with other business intelligence solutions (ERP, CRM software, etc.)
We also offer different cooperation models. Choose the one that is most suitable for you
- software development from scratch;
- dedicated team;
- team extension.
Bottom line on POS security
Point-of-sale security is one of the major sticking points you should pay attention to while developing your solution.
Keep that in mind because data breaches and other types of hacker attacks are real security threats to product integrity and reputation. So, creating a POS security solution should become your priority.
We suggest taking POS security seriously. You can’t overdo safety measures, as a lot is at stake here, and cybercriminals are always looking for new “opportunities” to pounce on, and constantly honing their knowledge, skills and only getting “better” as time passes.
FAQ
A Point of Sale (POS) attack is a type of cyberattack that targets the systems used to process payment card transactions, such as credit or debit cards, at physical locations like retail stores, restaurants, and gas stations.
These systems, known as POS terminals or POS systems, are responsible for capturing and processing card information when a customer makes a purchase. A POS attack typically involves hackers infiltrating these systems to steal sensitive payment card data.
POS systems are often targets for malicious software. Such malignant software penetrates the system and steals credit card information that is being processed by POS terminals.
The main compliance standard for Point of Sale (POS) security is the Payment Card Industry Data Security Standard (PCI DSS). This set of security requirements is designed to ensure that all entities involved in processing, storing, or transmitting cardholder data (including merchants using POS systems) maintain a secure environment to protect sensitive payment information.
POS is typically targeted by malware that steals credit card information, which can later translate into credit card fraud, i.e. used for unauthorized payments in the future.